Introduction to Cloudflare
Cloudflare is a leading provider of content delivery network (CDN) and network security services. Its platform helps users accelerate website performance, defend against DDoS attacks, and improve reliability through a wide range of tools, including SSL/TLS encryption, DNS management, and traffic analytics.
With its globally distributed data centers, Cloudflare ensures faster page load time, stronger protection, and flexible solutions for projects of all sizes—from personal blogs to enterprise-scale applications.
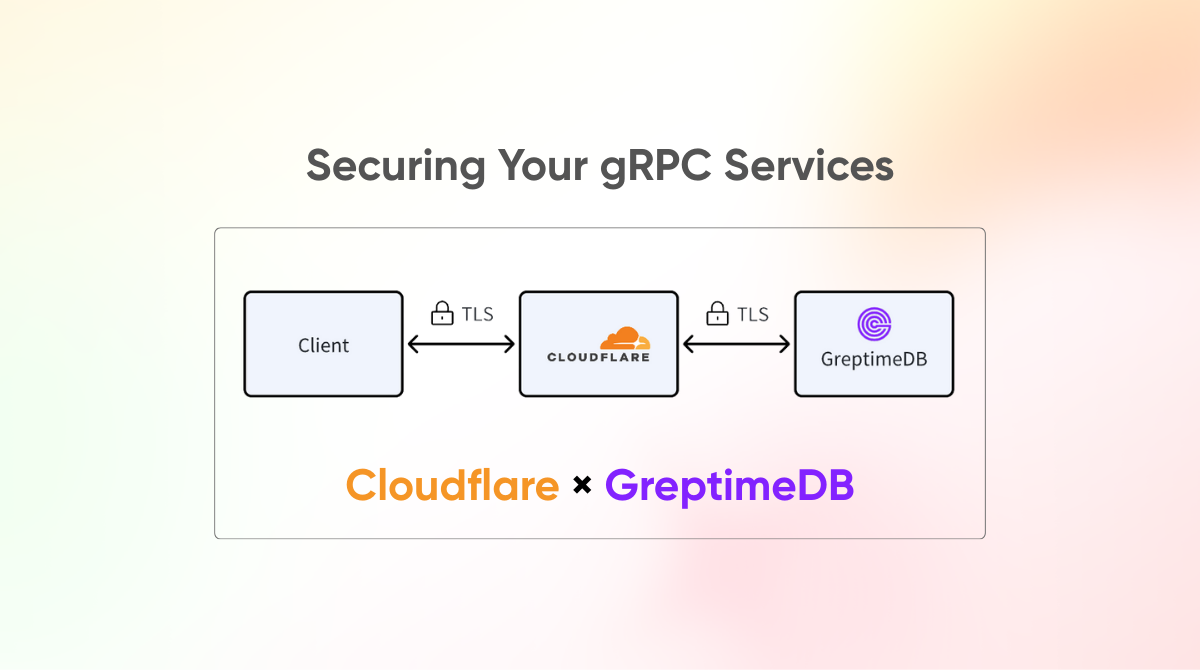
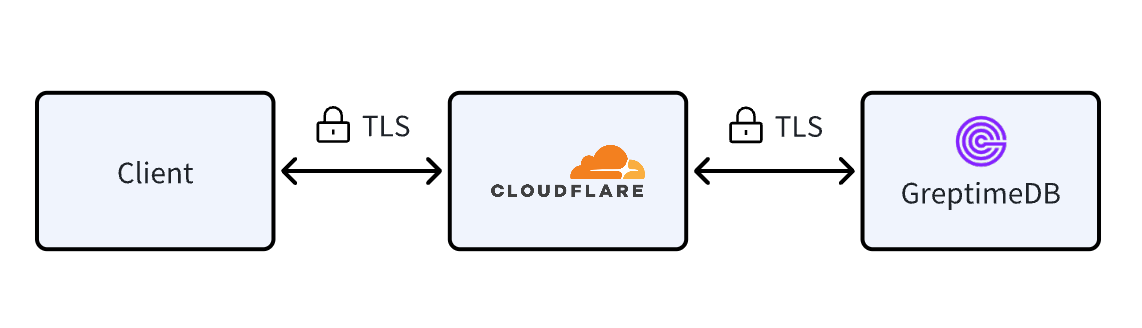
In this article, we’ll walk through how to use Cloudflare as a reverse proxy for GreptimeDB, enabling stronger security, encrypted access, and enhanced observability.
Configuring Cloudflare
1. Domain Hosting
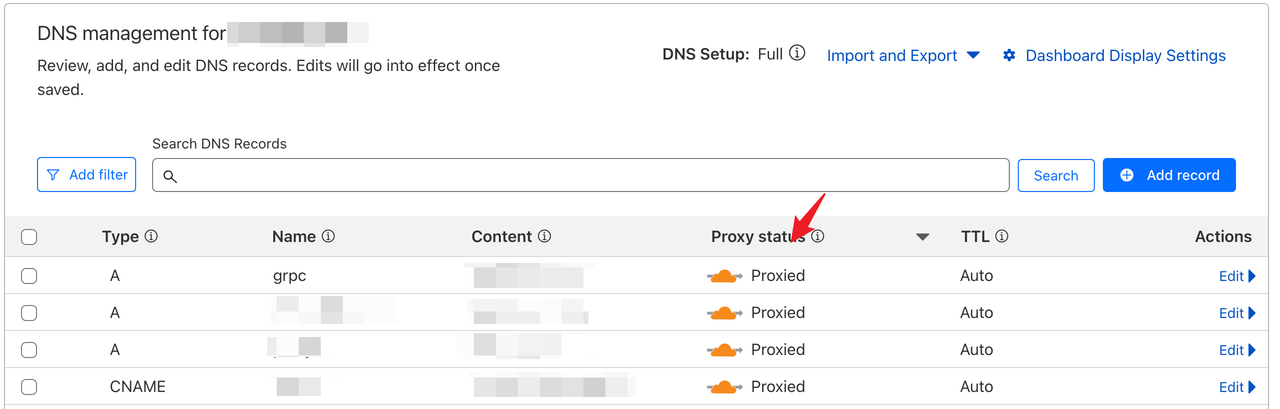
First, ensure your domain is properly hosted on Cloudflare. Follow the official documentation to add and manage your domain.
Set the DNS record’s proxy status to Proxied (also called Orange Clouded).
In this guide, we use grpc.some-domain.com as an example, which is configured as an A record pointing to the GreptimeDB server’s IP address.
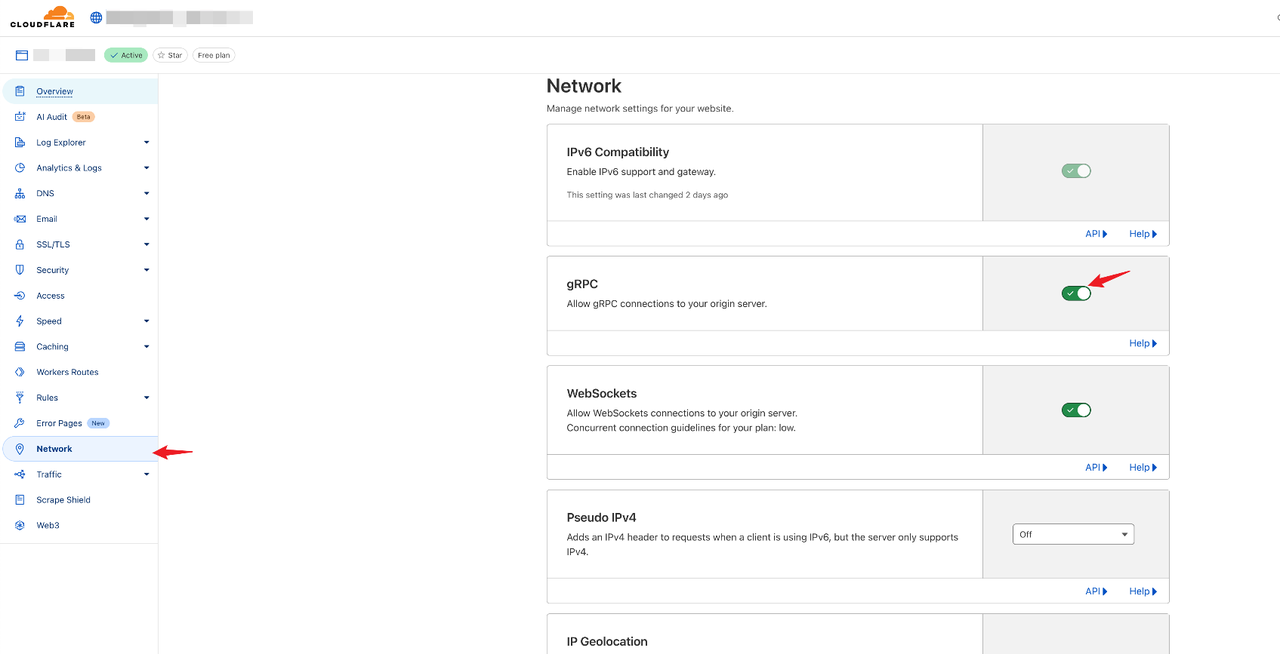
2. Enable gRPC Proxy Support
By default, Cloudflare does not proxy gRPC traffic. You’ll need to manually enable gRPC proxying in the domain's Network settings. Refer to the Cloudflare gRPC documentation for more details.
3. Configure SSL/TLS Certificates
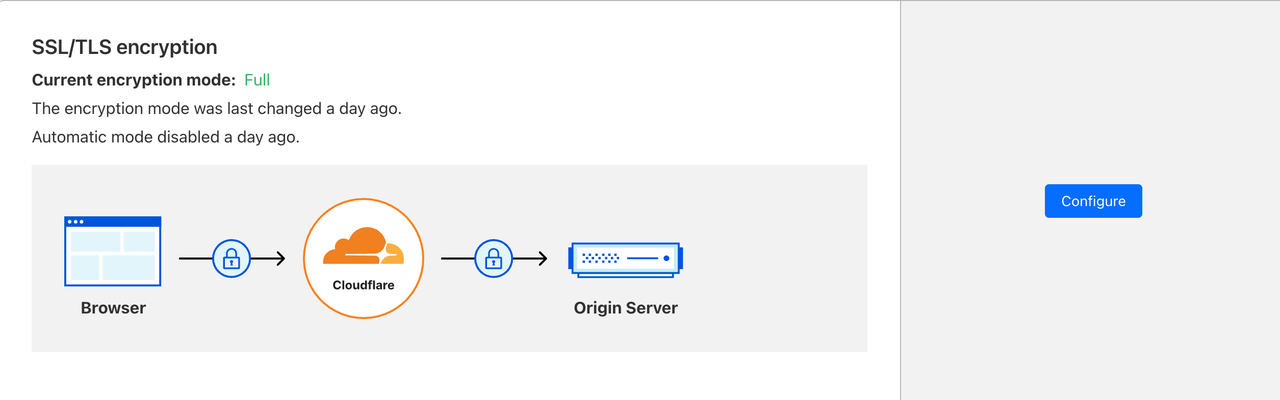
Go to the SSL/TLS settings in your Cloudflare dashboard and set the encryption mode to Full. This ensures that both connections—between client and Cloudflare, and Cloudflare to the origin are secured with TLS.
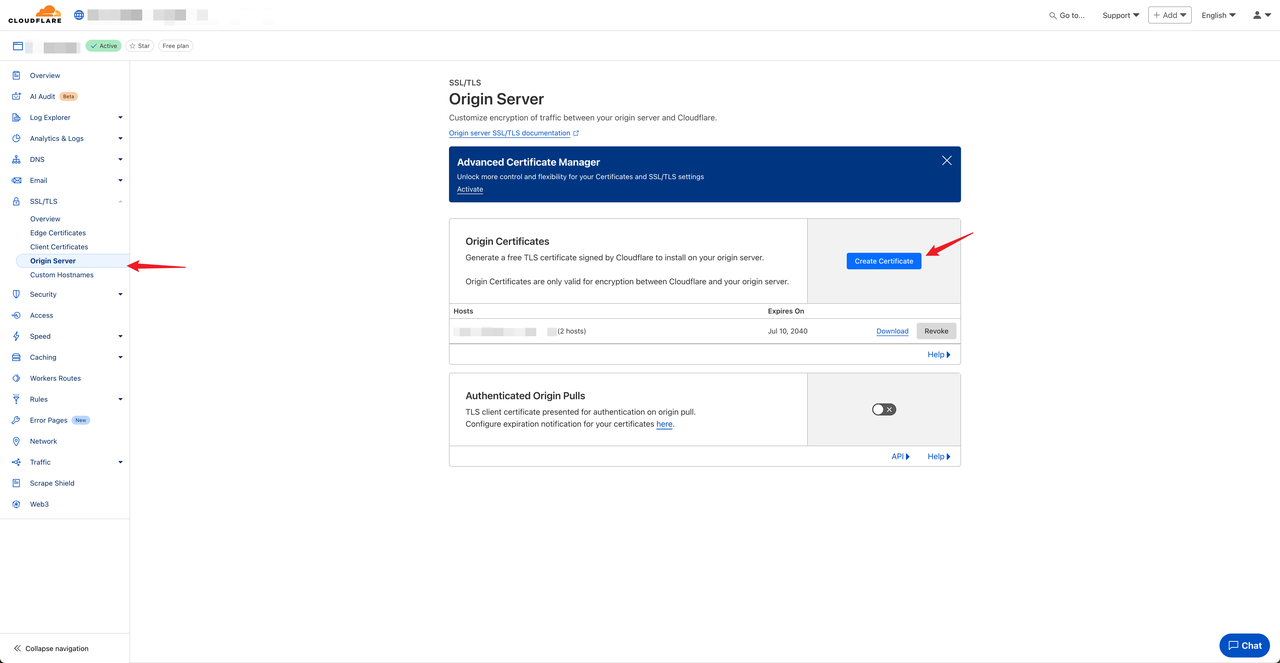
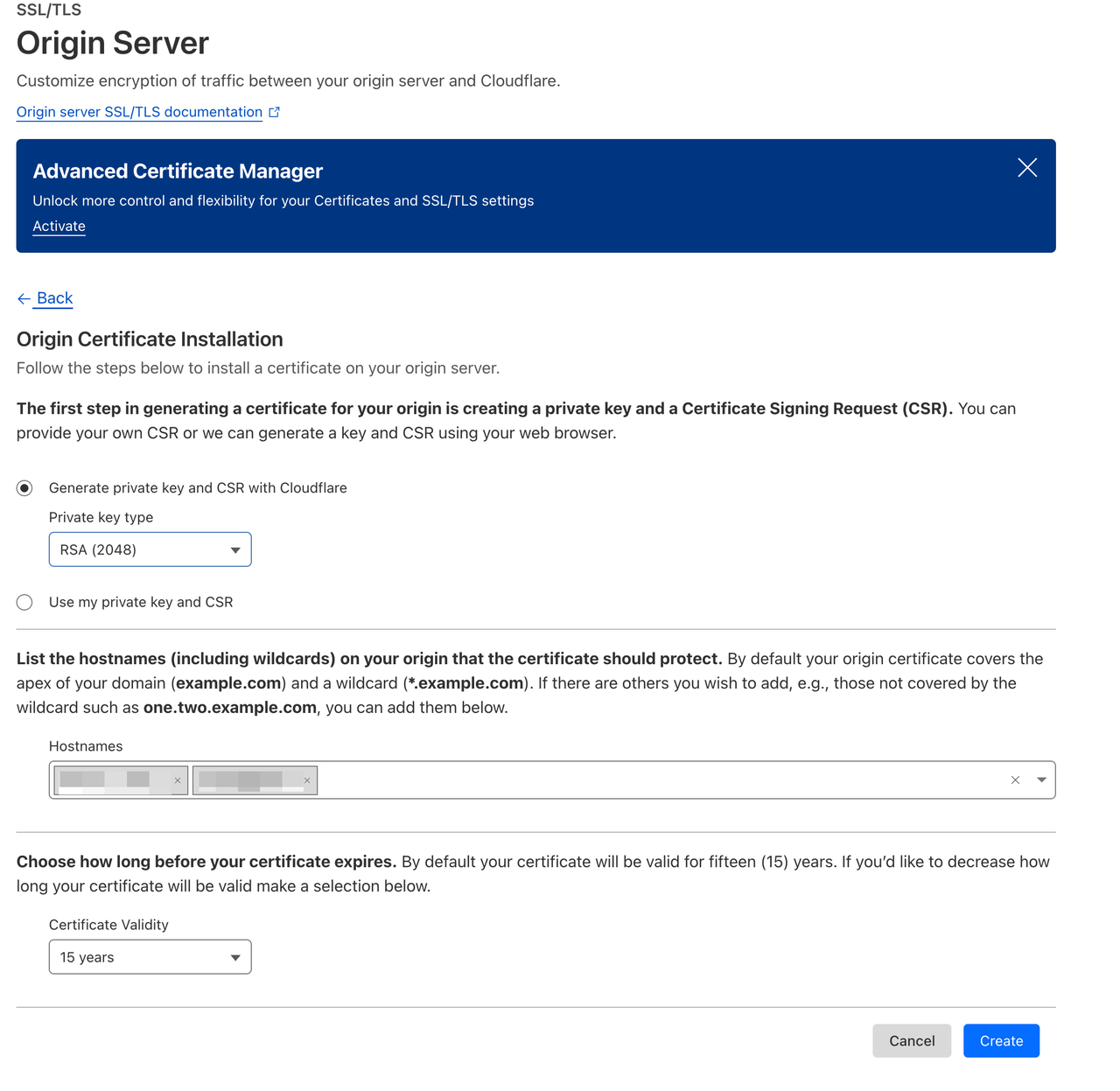
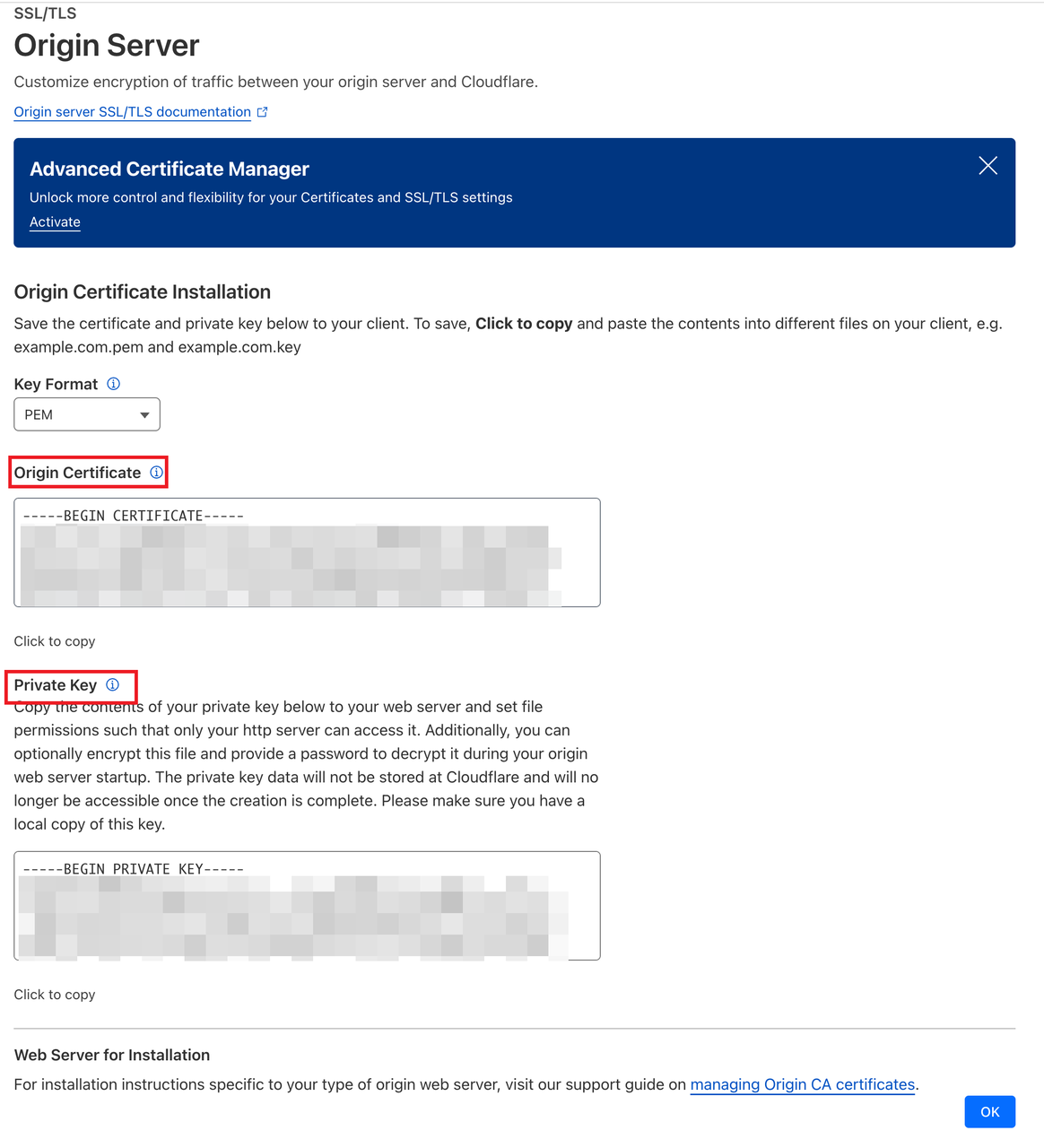
Next, under SSL/TLS → Origin Server, create a new origin certificate. Cloudflare will generate a certificate and private key, which you should save securely.
Note: See the Cloudflare Origin CA guide for detailed instructions.
Install Certificates on GreptimeDB
On your GreptimeDB server, place the certificate and private key in a secure directory, such as /etc/ssl/certs/greptimedb.crt and /etc/ssl/private/greptimedb.key.
Then, update the GreptimeDB configuration file. In the [grpc] section, configure the following:
[grpc]
bind_addr = "0.0.0.0:443"
[grpc.tls]
mode = "require"
cert_path = "/etc/ssl/certs/greptimedb.crt"
key_path = "/etc/ssl/private/greptimedb.key"Note:
- Cloudflare proxies gRPC traffic only on port 443, so GreptimeDB must listen on that port.
- TLS mode should be set to required.
- Ensure the correct paths for
cert_pathandkey_path.
Writing Data via Secure TLS Connections
Once Cloudflare is configured and the server certificate installed, clients only need to enable TLS to securely connect to GreptimeDB.
For example, using the GreptimeDB Java Ingester SDK, you can configure the client with TLS support by setting TlsOptions when building GreptimeOptions(see line 18):
public class LowLevelApiWriteQuickStart {
private static final Logger LOG = LoggerFactory.getLogger(LowLevelApiWriteQuickStart.class);
public static void main(String[] args) throws ExecutionException, InterruptedException {
GreptimeOptions opts = GreptimeOptions.newBuilder("grpc.huanglei.rocks:443", "public") // Optional, the default value is fine.
.asyncPool(new SerializingExecutor("async_pool"))
.rpcOptions(RpcOptions.newDefault())
.writeMaxRetries(1)
.maxInFlightWritePoints(10 * 65536)
.writeLimitedPolicy(LimitedPolicy.defaultWriteLimitedPolicy())
.defaultStreamMaxWritePointsPerSecond(10 * 65536)
.useZeroCopyWriteInBulkWrite(true)
.routeTableRefreshPeriodSeconds(-1)
.checkHealthTimeoutMs(1000)
.router(null)
.authInfo(AuthInfo.noAuthorization())
// Specify the use of TLS to verify the server's identity. The default configuration is used here, which means reading the system's CA certificates.
.tlsOptions(new TlsOptions())
.build();
final GreptimeDB greptimeDB = GreptimeDB.create(opts);
TableSchema cpuMetricSchema = TableSchema.newBuilder("cpu_metric")
.addTag("host", DataType.String)
.addTimestamp("ts", DataType.TimestampMillisecond)
.addField("cpu_user", DataType.Float64)
.addField("cpu_sys", DataType.Float64)
.build();
TableSchema memMetricSchema = TableSchema.newBuilder("mem_metric")
.addTag("host", DataType.String)
.addTimestamp("ts", DataType.TimestampMillisecond)
.addField("mem_usage", DataType.Float64)
.build();
Table cpuMetric = Table.from(cpuMetricSchema);
Table memMetric = Table.from(memMetricSchema);
for (int i = 0; i < 10; i++) {
String host = "127.0.0." + i;
long ts = System.currentTimeMillis();
double cpuUser = i + 0.1;
double cpuSys = i + 0.12;
cpuMetric.addRow(host, ts, cpuUser, cpuSys);
}
for (int i = 0; i < 10; i++) {
String host = "127.0.0." + i;
long ts = System.currentTimeMillis();
double memUsage = i + 0.2;
memMetric.addRow(host, ts, memUsage);
}
cpuMetric.complete();
memMetric.complete();
CompletableFuture<Result<WriteOk, Err>> future = greptimeDB.write(cpuMetric, memMetric);
Result<WriteOk, Err> result = future.get();
Result<Integer, String> simpleResult =
result.map(WriteOk::getSuccess).mapErr(err -> err.getError().getMessage());
if (simpleResult.isOk()) {
LOG.info("Write success: {}", simpleResult.getOk());
} else {
LOG.error("Failed to write: {}", simpleResult.getErr());
}
List<Table> delete_objs = Arrays.asList(cpuMetric.subRange(0, 5), memMetric.subRange(0, 5));
// We can also delete data from the table using the `WriteOp.Delete`.
Result<WriteOk, Err> deletes =
greptimeDB.write(delete_objs, WriteOp.Delete).get();
if (deletes.isOk()) {
LOG.info("Delete result: {}", result.getOk());
} else {
LOG.error("Failed to delete: {}", result.getErr());
}
greptimeDB.shutdownGracefully();
}
}Conclusion
By setting up Cloudflare as a reverse proxy for GreptimeDB’s gRPC service, you can:
- Enforce end-to-end TLS encryption, ensuring data confidentiality and integrity.
- Hide the origin server’s IP address, reducing the attack surface.
- Benefit from Cloudflare’s auditing and observability features.
Keep in mind that Cloudflare’s free plan provides only one managed domain and one free SSL certificate (via Let’s Encrypt). For advanced needs—such as hosting multiple domains or using custom SSL certificates—you’ll need to upgrade to Cloudflare’s Business Plan or use the Advanced Certificate Manager.